Windows 11 on the Pixel 6! Microsoft finally has the phone OS it has always wanted.
Here’s a fun new feature of Android 13: working virtualization support. Google is building virtualization into Android for its own reasons, but Android developer kdrag0n has commandeered the feature to boot ARM Windows 11 and desktop Linux. The developer even got the Windows version of Doom running, all inside a VM on the Pixel 6.
kdrag0n says that Android 13 has “full KVM functionality” at “near-native performance.” You need root to enable the functionality, which doesn’t support GPU acceleration. The functionality also doesn’t support nested virtualization, so while you can now run Android on Windows and Windows on Android, making an infinitely nested OS turducken is out of the question.
This makes for a neat demo that’s not at all what Google wants to do with Android’s upcoming VM support. Esper’s Mishaal Rahman has been meticulously tracking Android’s virtualization progress for some time now, and the apparent plan is to someday (maybe in Android 13) use virtual machines as a security and privacy sandbox for various features. Imagine instead of processing sensitive data at the normal app permission level, the data could be processed in a separate OS, so any attackers would have to break through the app security model, then Android, then the hypervisor, then this other, private OS.
Yes, it runs Doom (connecting to the phone’s Windows VM from my computer for keyboard input) pic.twitter.com/6PORUnJk8m
— kdrag0n (@kdrag0n) February 14, 2022
The first part of Google’s virtualization work is standardizing the Linux kernel shipped with an Android device. Today, the kernel on Android is Android’s usual story of fragmentation, with every individual phone model shipping a custom version of the Linux kernel loaded with specific changes and drives. Kernels basically never get updated, and it’s very hard to roll out any virtualization features at an OS level when literally 10,000+ different Android kernels are out there. Google’s plan to standardize the Linux kernel is called the “GKI” or “Generic Kernel Image.”
The Generic Kernel is the Android kernel with as few changes as possible, and any manufacturer changes or hardware support is done via a module system. Now the main kernel is standardized and has a known set of features. One day, the kernel may even be updatable. The GKI is shipping first on the Pixel 6, which is why the Pixel 6 is the first (and so far only) Android phone that can do this.
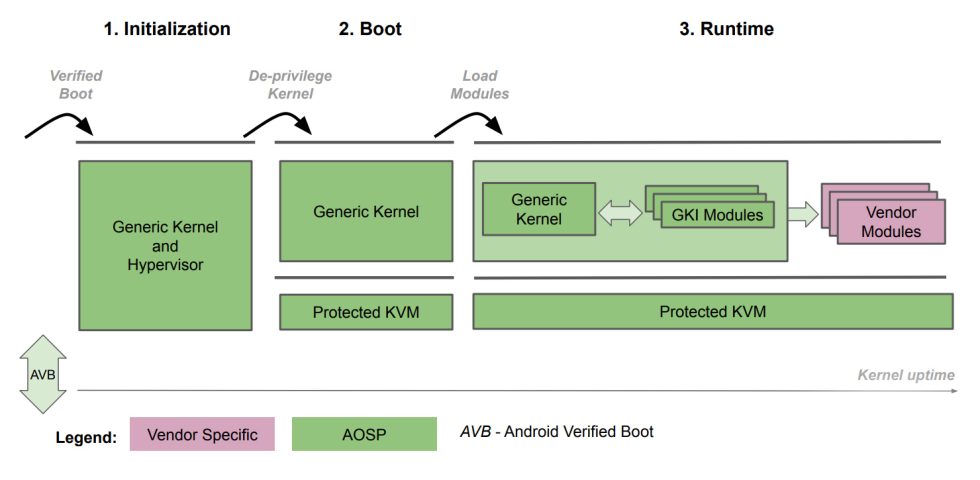
Google is adopting the Linux kernel’s KVM and Chrome OS’s virtual machine manager, crosvm. The company is also building a headless, stripped-down version of Android to run in a VM.
Previously, this tiny OS was thought to go by the name “Microdroid,” but that moniker just seems to be a label in Google’s VM software. The more accurate name appears to be “CompOS,” as in an OS meant for performing isolated compilation. All of this code will eventually be shipped to every Android phone via a new “virt” Mainline module.
Google imagines running the main Android distribution and the protected VM on the device hypervisor, making the VM data a whole extra level of private and secure from even the most restrictive Android settings. For starters, Google wants to use it as a replacement for ARM’s TrustZone (running things like DRM) and cryptography work. Google wants to get rid of TrustZone because TrustZone is full of highly privileged third-party proprietary code and because TrustZone is slow. With a faster secure environment to do work in, Google could start doing more time-sensitive tasks like voice recognition in one of these private VMs. So far, the company seems like it’s making progress!
Listing image by Andrew Cunningham



